A few days ago, I got a call from my girlfriend, Olivia. I was so deep in working on my startup, Parse.ly, that I hadn’t checked my bank account statements in several weeks. We just went into private beta last Thursday, after DreamIt Demo Day. She noticed some suspicious charges, and so I looked into them. Indeed, it looked like I had been a victim of fraud: there were three charges that clearly was not me.
I immediately called Chase Customer Service. In order to confirm the details about my account, the representative needed me to identify the fraudulent charges, but also identify charges that were actually valid. For this latter bit, I needed to identify the time/place of a specific transaction. This card was mostly used for online auto bill payments, so this turned out to be impossible for any of my last 20 valid payments. Yet the customer service rep insisted that I name a time and place. I told her, “The time and place was whenever the server for this system decided to automatically bill my account. I don’t know where their server is, I don’t know what time their cron jobs run.”
“Cron jobs?” she said.
Right, I had been hanging around techies at DreamIt Ventures for too long. “Listen, the transaction didn’t take place physically, it took place digitally. I can identify one transaction, which is about a month old, where I actually used the card in-person to buy something.” She finally understood and let me move on.
Burak from Trendsta said he felt bad for me, for how patient I had to be with this person. But that was the least of it. This little technical misunderstanding was nothing compared to what followed.
I was told that in order to get a credit back from my account, they had to collect from me a signed affidavit indicating the charges were fraudulent. This affadavit would be “securely shared” with me via e-mail. OK, “sounds good” I said. I waited around for the e-mail to come in.
Finally, two e-mails arrived in my inbox. The important bits are in red. First:
Message from Chase Customer Claims Secure Document Exchange
From: [email protected]
Welcome to the Chase Customer Claims Secure Document Exchange. You recently contacted Chase regarding your claim number XXXX. Your documents are available for your review.
Per our telephone conversation, you will need to register to our secure website.
Your initial password is: passwordYour initial user name has been sent to you in a separate email.
On your first log in, you will be required to select a new password.
Thank you for using Chase Customer Claims Secure Document Exchange.
To contact Chase for claim related questions or to withdraw your claim, please call 1-866-564-2262.
Any geek reading this will immediately identify some key things wrong with this e-mail that make it look like a total phishing expedition. Namely:
- The e-mail address, rather than being from a chase.com domain, was from a strange domain named “secure-dx.com”.
- Rather than sending a cryptographically secure, expiring activation link, a default password was sent in plain text.
- To make matters worse, the password is the same for all users, and thus anyone who can guess my e-mail address can easily impersonate me on this “secure document” website.
- The default password is “password”. WTF?! I mean, c’mon?
I didn’t quite understand why I needed a “second e-mail” now, but I opened it up. Here it is, excerpted:
Your Chase Customer Claims Secure Document Exchange Electronic Package is available online
From: [email protected]
ANDREW MONTALENTI,
Welcome to the Chase Customer Claims Secure Document Exchange.You recently contacted Chase regarding your claim number XXXX. Your documents are available for your review.
Per our telephone conversation, you will need to register to our secure website by clicking on the link below or copy and paste the link into your browser’s address bar.
https://chase.secure-dx.com/consumerdcx-chase_atm
Your user name is [email protected]
Your initial password has been sent to you in a separate email
On your first log in, you will be required to select a new password. NOTE: This site is different from Chase.com and passwords are not related. Updating your password on Chase Customer Claims Secure Document Exchange will have no impact on established Chase.com passwords.
Once registered, you will be able to access your customer correspondence on our secure website. You may be offered the option to complete and sign the form online if you wish to do so. […]
To say I was confused would be a major understatement. I was downright depressed.
My guess is that the engineers at Chase thought that by separating the “password e-mail” from the “user e-mail”, that somehow made the whole communication more secure. Two e-mails are better than one, right?
The most important thing to point to is the link. The link where this secure communication will happen is not at the chase.com domain Instead, it is at https://chase.secure-dx.com/consumerdcx-chase_atm. There is no way, NO WAY this is a real Chase site, I think.
I click on the link and in Firefox, I see this:
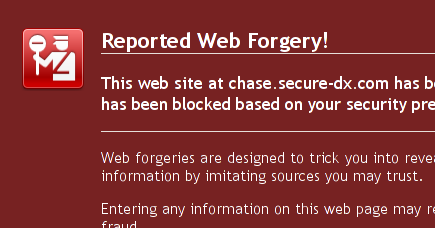
At this point, my paranoid self turns on. Curious, I click through the link anyway. And I see this:
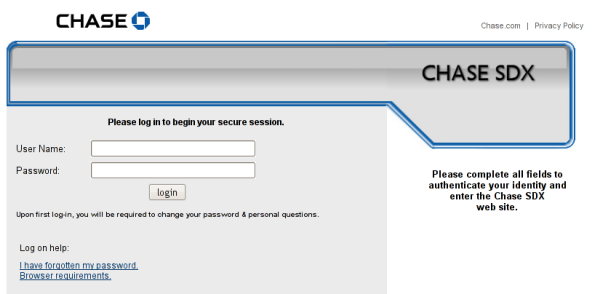
Now I’m really paranoid. Links off secure-dx.com pointing back to chase.com’s privacy policy. A username and password box and a sort of hokey imitation of the Chase.com web design. I realize, holy shit, I’m being duped! Not just small-time credit card fraud, but someone has managed to really take over my life!
Why am I freaking out? The customer service person I talked to, I realize what must have happened. That wasn’t Chase. Someone stole my credit card information and then set up a call forwarding on my cell phone, somehow, to point Chase’s customer service number to some fraudulent interceptor. This person then diligently took my claim only to send me an e-mail that would get yet more information out of me and take me for even more money. I freaked!
Immediately, I double-checked my call logs and compared them to Chase.com customer service numbers. I made sure to change my DNS server to OpenDNS to make sure no one was somehow intercepting that. Finally, I realized I could look at the number written on the back of my Chase credit cards. It all checked out — the number was good. So I switched phone. I called Chase customer service on both my phone and Olivia’s. I made sure the messages were exactly the same. From Olivia’s phone, I called back Chase again to speak to someone there about this. But then I got even more paranoid — how big could this be? — so I decided to hang up. Instead, I called my local Chase branch in my neighborhood.
With my local branch’s help, I got transferred via a branch office line to the actual Chase customer service. Finally on a secure line, I thought to myself. When they picked up, I was expecting to uncover the scam of the century. I felt like an investigative journalist right on the tail of something truly big.
But then I spoke to the Chase representative, on the secure line, and she explained to me that this is just the normal procedure. secure-dx.com is the website they use for “securely” sharing documents.
I was livid. I explained everything wrong with this setup. I demanded to speak to a supervisor. I spoke to a supervisor. He said he did not know why the system was the way it was. He wasn’t a software guy. He just knew that “with the way the business is changing lately, a lot of systems are in flux.” I said this flux was unacceptable. “I’m a software engineer,” I said. “How can I possibly trust Chase to manage my financial accounts if something as simple as sharing a PDF document is done in the least secure way possible?” What other skeletons might they have in the closet?
I wanted to be forwarded to the department responsible for that. After my explanation to him of what was wrong, he fully understood the problem. To his credit, he admitted it was wrong the way it was set up. He actually tried to track down a supervisor. But there was none that could field IT and software requests.
They promised to call me once they could track someone down to talk about this. No call yet.
My excitement came down a couple of notches. I was not the investigative journalist undercovering an elaborate scam any longer. Instead, I was a software engineer. And some members of my profession have let me down. Big time.
In the meanwhile, I did the research and found the vendor who provided this service to Chase. They are Wolters Kluwer, a “financial services and banking compliance solutions provider”. The product page for “SDX”, Secure Document Exchange, is completely ludicrous. They claim this product includes “industry-leading security, including PKI encryption and multi-level user authentication, to keep communications safe at every step of the process.”
Right, so the password was sent in plain text. The default password is “password”. And, rather than having a chase.com subdomain which points at Wolters Kluwer’s server (e.g. secure-dx.chase.com) and sharing a secure chase.com certificate with them, they decide to host the whole thing outside of the chase.com domain, so that as a user, I have no way of confirming this actually is an e-mail or system originating from Chase. Users are so confused by this that they have already reported it as a phishing scam, even though it is not one.
That’s industry-leading? That’s “safe communication”?
No, that’s a joke. Chase should be ashamed.
Jan 5, 2013 Update: Hi, unexpected /r/programming visitors! Yes, this article is over three years old. Yes, this process has not changed much in the past three years. No, I did not expect a customer support representative to really know what a cron job was.
Many reddit commenters took the position that I was being “overly paranoid” and that I took this whole thing way too seriously. Well, I strongly disagree. As many other commenters rightly pointed out, many individuals share usernames / passwords across systems. It was not paranoid for me to think this was actually a phishing scheme. Why would a phishing scheme send me a password, only to have me reset it when I log in? Answer: out of the hope that some percentage of users would “reset” their password with their actual bank password, of course. Phishing schemes are most effective when they spoon feed users a little trust, and then betray it. I admit that thinking that my cell phone had been hacked was perhaps a leap of true paranoia, but I tried to convey how I actually felt.
Chase did finally introduce their own domain (https://sdx.chase.com) for their “secure” document exchange service, the lack of which which was, by far, the major sore spot in this whole setup. The rest of the silly process remains. For me, the greatest damage this process does is in conditioning novice Internet users that systems like this are trustworthy. In other words, I’m not upset about the hundreds of people who, like me, questioned the legitimacy of this system. I’m upset about the thousands, or possibly millions, who used it without questioning it at all.
For those of you who enjoyed the article and feel as a programmer you would never make the same mistakes, you can take a look at the job opportunities available over at my startup, Parse.ly. A tad opportunistic, but hey, it’s not every day thousands of programmers flock to my blog.

Just want to reiterate how unbelievable it is that they are still using this system. Making me want to close Chase accounts, to be honest…
Wow. I also got this email from Chase after reporting transactions whichever I didn’t make on both my debit card and credit card in 2 weeks. I saw the email domain wasn’t something.chase.com so I got suspicious. As long as I get a new card in a few days and the charges made in my accounts get reverted back, I don’t see the need to even check on the “secured” document on the claim.
Just got this email after a month of fadulent charges. Already have my new card. Its leading me to https://sdx.chase.com which I should trust I guess but yeah the temp password is in plain text. All of this is so weird. The account should be managed through my banking account through chase.com IMO. I’m simply shocked this is happening in 2017.
I’m in the club, too. Like all of you, I was concerned it was an elaborate phishing scam, especially after my my debit card was hacked. I took the email in to my local branch and was told to forward it to [email protected]. They confirmed that it’s a legit email so I completed the process online. It’s amazing to me that Chase hasn’t improved this process in 8 years — think of all the wasted time!
Received the same message from secure-dx.com today and was greatly surprised, then found your post on google.
it’s still happening on 2017..
I dealt with this today. The first time I called, the Chase representative told me it was not associated with Chase. Which is what I’d suspected, but then I noticed and pointed out that the domain was sdx.chase.com. He stuck to his story. I work in IT, so I was like, well, then someone has compromised Chase’s DNS then. After that call, I found this post and the comments, and I called Chase back. The second representative told me it WAS Chase, and even looked up the claim number in the email, tracing it back to a matter that was closed weeks ago.
So yes, this is Chase. And it’s terrible. I’m sending a note to [email protected], I’m not sure if they’ll care or do anything about it, but it’s really scary bad to nerds like us.
Received this email today – every security minded instinct screaming it’s a phishing attempt. Googled around and found your article on it. In fact they are still using the same secure-dx domain, they should really fix this!!
The biggest fact that restores faith this is real is the fact they already have your data at the secure site. It doesn’t ask for you to enter something they could use against you but instead gives you the data. This indicated they already had it and thus it’s legit if foolishly done.
Just received this sketchy looking email as well. Same story as most here, add the fraudulent activity is occurring around my transition to a new smart device. I got the usual Chase text messages about fraudulent activity – and did follow up over the phone with a less-than-impressive agent whom I vaguely distrusted. As an IT officer, none of this bodes well from even a Luddite perspective – the laziness and flagrant disregard of providing a genuine security UX will serve to prevent me from going any further. Same SDX veil.
I got the same email and had a roller-coaster ride. Conclusion; it’s legit. I had already been a scam victim and on top of it – this, was a real pain. I copied the email and sent a message from Chase’s secure message after logged in. Surprisingly they replied it was legitimate. No further explanation, though. I still couldn’t believe it and thought through other possible scenarios. But after reading this page and other few threads, now I believe it is. Very poorly operated, though. As in many companies, they don’t care or reform the system or operation unless the particular department makes profit. This is definitely not to the bank. It’s our, consumers’ problem and they don’t care. They were not helpful with my original rip-off scam either, again they don’t make profit out of it. Such is a bank. Is there any decent bank?
Still happening as of 2018, really caught my eye and knew immediately not to touch anything in the email. There’s a small chance this could be a part of chases claims systems, but I would personally play it safe and just talk to someone over the phone to make any changes.
I was sent this identical email in Jan 2024–not from Chase but from a local bank I use. This “security” approach is still being used. Un-friggin-believable.